Articles - Security (4)
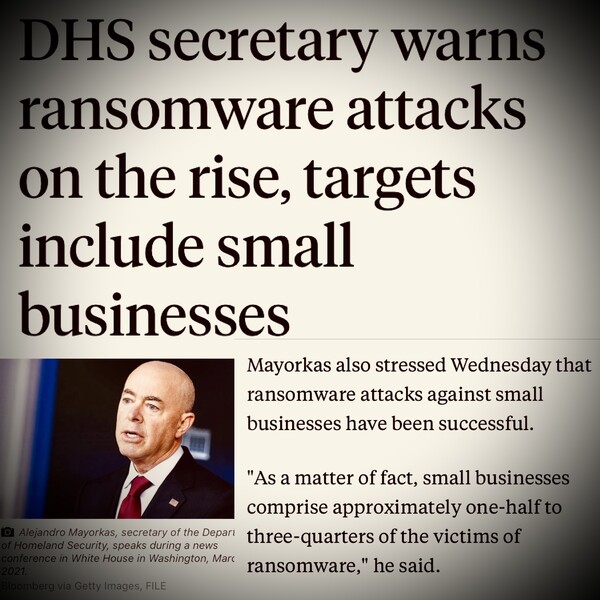
Small Businesses Are Ransomware Targets
Is your business too small to be targeted by ransomware? Unfortunately, bad actors are equal opportunity criminals, and do not discriminate about the size of their victims’ companies. In fact, many of these criminals target small businesses for exactly this reason. No business is too small. ...
Staying Safe From Phishing and Spear-Phishing
Do you know how to protect yourself against digital scams? Phishing – the practice of using email lures to fish for passwords, credit card numbers, and other personal information from a sea of users – has been around since 1996. Still, most people were not aware of the problem for five years until ...
How Employees Can Protect Themselves From Phishing Attacks
A whopping 80% to 90% of cyberattacks start with phishing. Why does this matter? Because even the best cybersecurity can’t stop all phishing from happening. While adding the proper security and safety can greatly reduce the unwanted emails that get through, it’s not infallible. That’s why it’s up ...
Ransomware Is Preventable
Unfortunately it’s become more common to hear about major ransomware attacks and companies that have been hacked. It’s a grim reminder that companies and networks can be attacked at any time with serious impacts. While it could be unlikely that your business is attacked and extorted for money by a ...
How to Spot and Protect Yourself from Phishing
Is cybersecurity a new concept for you? Or are you a computer-savvy user who knows just what to do to protect yourself? Either way, you may be more vulnerable than you think. “Phishing” attacks—email requests for sensitive information—are growing more common today. Plus, they are becoming more and ...