Articles
Does Your Small Business Need an IT Department?
If you own, manage or are part of a small business, you may find yourself wondering if you need a designated IT employee or an IT department. It is not a question of whether IT concerns will arise but a matter of when, how often, and how problematic they will be. We've all been there and ...
What Are Managed IT Services?
If you are part of a small business, you know there is a lot to manage, and often job duties and responsibilities are plentiful, which can cause some owners and employees to become overwhelmed with an increasing workload. It is often helpful to outsource some responsibilities you may not have the ...
Time to Update Your Software and Operating System?
When you are focused on growing your business, staying up to date with software and operating system updates might not be at the top of your to-do list. However, neglecting these updates can have serious consequences for your organization. As Bret Arsenault, Chief Information Security Officer ...
Hybrid Workplaces Require New Security Measures
Hybrid workplaces are here to stay and the spectrum of office configurations requires a new approach to network security. Many companies are adapting by limiting their physical footprint with the use of “Flexwork Space.” Flexwork spaces are smaller, multi-purpose, cross-functional spaces and ...
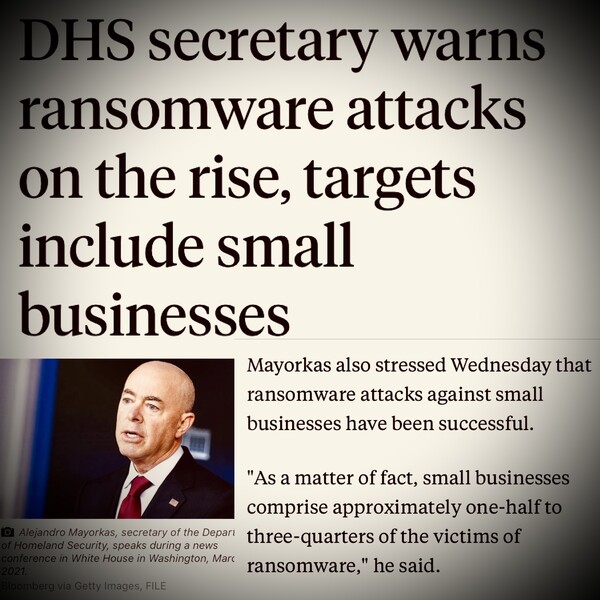
Small Businesses Are Ransomware Targets
Is your business too small to be targeted by ransomware? Unfortunately, bad actors are equal opportunity criminals, and do not discriminate about the size of their victims’ companies. In fact, many of these criminals target small businesses for exactly this reason. No business is too small. ...